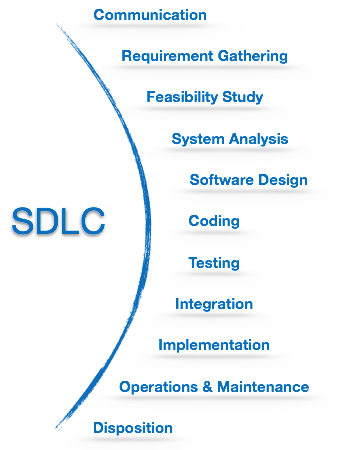
1.Why Flow Analysis Matters More Than Ever
In today’s fast-paced software landscape, the complexity of applications has grown exponentially. Modern systems integrate APIs, microservices, and AI models — creating intricate data flows that can easily conceal hidden bugs or security vulnerabilities. For organizations prioritizing code quality and cybersecurity, flow analysis has become a foundational technique to ensure software reliability.
Flow analysis refers to the process of examining how data moves through a program — across functions, modules, and system boundaries. By understanding the logical “flow” of information, developers can detect potential vulnerabilities such as memory leaks, injection flaws, and data exposure before they reach production.
In this blog, we’ll explore the critical role of flow analysis in software development, the difference between static and dynamic analysis, tools like SonarQube and CodeQL, and how teams integrate these methods within Agile and CI/CD pipelines to prevent costly security breaches.
2. Understanding Flow Analysis
Flow analysis investigates how variables, data, and control structures interact across the life cycle of a program. Its primary goals are to:
- Detect anomalies early — such as undefined variables, unreachable code, and data leaks.
- Improve program efficiency by optimizing redundant computations.
- Identify security flaws like SQL injections, cross-site scripting, and buffer overflows.
- Ensure data integrity by tracing the origin and destination of sensitive information.
2.1 Types of Flow Analysis
Control Flow Analysis (CFA) – Examines the order in which instructions execute in the code.
Example: Identifying unreachable branches or infinite loops.
Data Flow Analysis (DFA)
– Tracks how variables are defined, used, and modified.
Example: Ensuring that user inputs are properly sanitized before database access.Information Flow Analysis (IFA)
– Focuses on the movement of sensitive or confidential data.
Example: Preventing unauthorized access to personally identifiable information (PII).
Each type plays a vital role in reducing bugs and minimizing security risks throughout the software lifecycle.
3. Importance of Flow Analysis for Detecting Bugs and Vulnerabilities
In software engineering, approximately 70–80% of software vulnerabilities stem from improper handling of data or logic flows. Flow analysis addresses this root cause by systematically inspecting how the code behaves under various conditions.
3.1 Early Detection Saves Costs
According to industry studies, fixing a bug after deployment costs 10x more than resolving it during the development phase. Automated flow analysis identifies issues early in the coding cycle, preventing expensive post-release patches and protecting brand reputation.
3.2 Enhancing Security Posture
Flow analysis identifies vulnerabilities before hackers exploit them. For example:
- Detecting tainted data that travels from an untrusted input source to a critical system component.
- Highlighting improper API calls that may expose endpoints.
- Pinpointing data flow leaks that could result in GDPR or HIPAA violations.
3.3 Improving Code Maintainability
Flow analysis also supports cleaner architecture. By visualizing dependencies and function calls, developers gain insights into code complexity, helping reduce technical debt and ensuring scalability.
4. Static vs. Dynamic Flow Analysis in Code
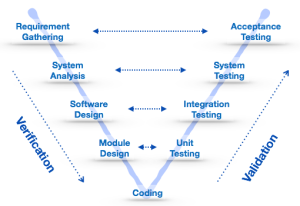
Both static and dynamic flow analysis play crucial roles in achieving comprehensive code security and reliability. The key difference lies in when and how they analyze the software.
4.1 Static Flow Analysis
Static flow analysis (SFA) inspects source code without executing it. It analyzes data and control flows using symbolic execution and abstract interpretation.
Advantages:
- Detects issues early (before runtime).
- Works across large codebases efficiently.
- Integrates seamlessly into IDEs and build systems.
Limitations:
- May produce false positives due to lack of runtime context.
- Can struggle with dynamically typed or interpreted languages.
Common Static Analysis Tools:
- SonarQube
- CodeQL
- Coverity
- Fortify Static Code Analyzer
4.2 Dynamic Flow Analysis
Dynamic flow analysis, on the other hand, observes program behavior during execution. It identifies bugs that occur only under specific runtime conditions, such as memory leaks or race conditions.
Advantages:
- Captures real-world runtime scenarios.
- Detects performance bottlenecks and concurrency issues.
- Validates actual data flow with concrete inputs.
Limitations:
- Requires comprehensive test cases.
- May introduce runtime overhead.
Popular Dynamic Analysis Tools:
- Valgrind
- AppDynamics
- Dynatrace
- Burp Suite (for security testing)
4.3 Combined Approach: Hybrid Flow Analysis
The most effective software teams employ a hybrid approach, combining static and dynamic methods to achieve full coverage — static analysis for breadth, dynamic analysis for depth.
5. Tools for Developers: SonarQube, CodeQL, and Beyond
5.1 SonarQube
SonarQube is one of the most widely used tools for continuous inspection of code quality. It performs static analysis to detect:
- Code smells
- Security hotspots
- Duplications and maintainability issues
SonarQube integrates with GitHub, GitLab, Bitbucket, and Jenkins, providing instant feedback via dashboards and pull request checks.
5.2 CodeQL
Developed by GitHub, CodeQL elevates static analysis to the next level. It converts code into a queryable database, allowing developers to write custom security queries.
Example use cases:
- Identifying data flow paths that lead to SQL injections.
- Detecting unvalidated input propagation.
- Scanning entire repositories for vulnerability patterns.
5.3 Other Tools Worth Mentioning
- Checkmarx – Focuses on SAST (Static Application Security Testing).
- Semgrep – Lightweight, open-source code pattern matcher.
- OWASP Dependency-Check – Detects known vulnerabilities in third-party libraries.
Each of these tools supports developers in integrating security analysis directly into their development lifecycle — aligning with DevSecOps principles.
6. Case Study: Preventing Security Breaches via Flow Analysis
Let’s consider a case study inspired by real-world scenarios in financial technology.
Background
A financial services provider noticed unusual access patterns in their internal reporting system. An investigation revealed a vulnerability in their code that allowed unauthorized users to retrieve transaction data — a clear data leakage issue.
Root Cause
The issue stemmed from improper data sanitization in one of the APIs. Sensitive data was passed from a backend service to a frontend report without proper role-based access checks.
Flow Analysis Application
The company implemented CodeQL queries to trace the data flow from input to output:
- Identified that unvalidated parameters traveled directly from API endpoints to report generation functions.
- Detected multiple unsafe variable assignments within the data transformation logic.
Outcome
- The vulnerability was patched before any significant data breach occurred.
- SonarQube and CodeQL were integrated into their CI/CD pipeline for continuous monitoring.
- Post-deployment reports showed a 65% reduction in critical vulnerabilities within three months.
This case illustrates how flow analysis, when properly implemented, can prevent multimillion-dollar breaches and strengthen compliance posture.
7. Role of Flow Analysis in Agile Development
In Agile environments, where releases happen in rapid iterations, code quality can easily degrade if not continuously monitored. Flow analysis ensures that security and quality evolve alongside agility.
7.1 Continuous Feedback
By embedding tools like SonarQube into Agile workflows, teams receive real-time feedback after every commit or pull request. This aligns perfectly with the Agile principle of continuous improvement.
7.2 Reducing Technical Debt
Frequent sprints often introduce shortcuts in coding practices. Flow analysis flags these issues instantly, preventing the accumulation of unmaintainable code.
7.3 Empowering Cross-Functional Teams
Flow analysis provides transparent, data-driven insights accessible to:
- Developers: Understand logical flaws and fix early.
- Testers: Design more effective test cases.
- Product Owners: Track code quality metrics over time.
In essence, it bridges the gap between velocity and quality.
8. Integration with CI/CD Pipelines
Integrating flow analysis into Continuous Integration/Continuous Deployment (CI/CD) ensures security and reliability are not afterthoughts — they are baked into the pipeline.
8.1 Typical Integration Flow
- Developer commits code →
- Static analysis (SonarQube/CodeQL) runs automatically →
- Reports generated for vulnerabilities or bugs →
- Build fails if issues exceed thresholds →
- Dynamic analysis runs in staging environment →
- Deployment proceeds only when security gates pass.
8.2 Benefits
- Automated Security Gates: Stop vulnerable code from deploying.
- Faster Release Cycles: Issues are caught early, minimizing rework.
- Compliance Readiness: Ensures audit trails for ISO, SOC 2, and GDPR compliance.
8.3 Example Setup
A DevOps pipeline using GitHub Actions + SonarQube + CodeQL can run parallel checks for:
- Code quality metrics.
- Security vulnerabilities.
- Dependency risk analysis.
This setup offers end-to-end assurance from development to deployment.
9. The Future of Code Analysis with AI
Artificial Intelligence is revolutionizing how developers perform flow analysis.
9.1 AI-Driven Insights
AI models can now:
- Predict potential bugs based on historical commit data.
- Auto-generate CodeQL queries.
- Detect previously unknown vulnerability patterns.
9.2 Machine Learning in Static Analysis
By learning from millions of codebases, ML-enhanced tools reduce false positives and adapt to new programming paradigms. For example:
- GitHub’s Copilot Autofix can suggest patches for detected vulnerabilities.
- AI-powered SAST tools can map complex data flows across microservices automatically.
9.3 Predictive Flow Analysis
Future systems will simulate how new code changes may affect existing data flows — enabling teams to forecast vulnerabilities before they occur.
9.4 Human + AI Collaboration
The ultimate goal is Augmented Secure Development — where AI assists, but human judgment validates. Developers remain in control, while AI accelerates detection and remediation.
10. Conclusion
Flow analysis is no longer optional — it is an essential component of modern software assurance. By integrating static and dynamic flow analysis, using tools like SonarQube and CodeQL, and embedding these practices into Agile and CI/CD pipelines, organizations can achieve:
✅ Fewer bugs
✅ Stronger security
✅ Faster releases
✅ Better compliance